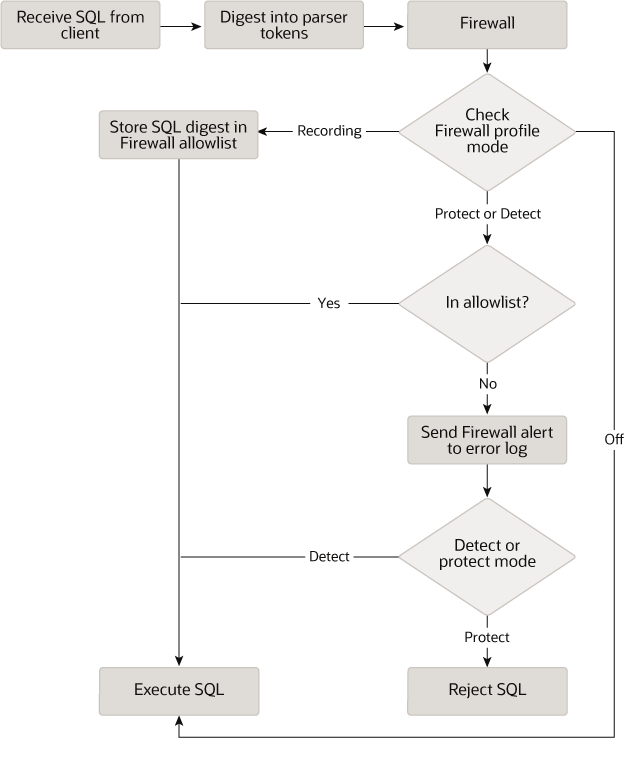
MySQL Enterprise Firewall 是一款功能强大的企业级数据库安全工具,它能够实时监控、检测和阻止对数据库的未授权访问和恶意活动,为 MySQL 数据库提供强大的安全保障。
它通过创建允许列表来定义可接受的 SQL 语句模式,根据这些模式匹配 SQL 语句来决定是否允许其执行,从而有效防范 SQL 注入攻击等安全威胁,且支持基于账户和组的配置文件,可针对不同用户或用户组制定特定的允许列表。此外,它还具备透明保护、高性能、高可用性和易于使用等特点。
MySQL Enterprise Firewall 核心要素
MySQL Enterprise Firewall 以插件库为基础构建,其核心要素如下。
服务器端名为 MYSQL FIREWALL 的插件会在 SQL 语句执行前对其进行审查,并依据已注册的防火墙配置文件来判定是执行还是拒绝每条语句。与之协同的还有名为 MYSQL FIREWALL USERS 和 MYSQL FIREWALL WHITELIST 的服务器端插件,它们借助性能架构及信息架构表,为查看已注册配置文件提供窗口。
为确保性能,配置文件会被缓存在内存中。防火墙数据库中的表则为防火墙数据提供支持存储,使配置文件能在服务器重启后依然保持有效,此防火墙数据库既可为 mysql 系统数据库,也可为自定义架构。存储过程负责执行诸多任务,像注册防火墙配置文件、设定其运行模式,以及管理防火墙数据在缓存与持久存储间的传输。
管理函数则为同步缓存与持久存储这类低层级任务,提供应用程序接口。系统变量用于防火墙的配置,而状态变量能给出运行时的操作信息。FIREWALL ADMIN 和 FIREWALL USER 权限,分别允许用户管理任意用户的防火墙规则,以及自身的防火墙规则。FIREWALL EXEMPT 权限则是让用户免受防火墙限制,例如数据库管理员配置防火墙时,开启此权限可防止因误操作把自己也锁在外,导致无法执行语句。
安装与配置
在 Linux 系统上,可运行位于 /usr/share/mysql-8.4/linux_install_firewall.sql 目录中的脚本进行安装。
1 2 mysql> \. /usr/share/mysql-8.4/linux_install_firewall.sql Query OK, 0 rows affected (0.00 sec)
该文件包含 5 张表和 7 个存储过程。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 bash-5.1# grep 'CREATE TABLE' linux_install_firewall.sql -A1 CREATE TABLE IF NOT EXISTS firewall_whitelist( -- CREATE TABLE IF NOT EXISTS firewall_group_allowlist( -- CREATE TABLE IF NOT EXISTS firewall_users( -- CREATE TABLE IF NOT EXISTS firewall_groups( -- CREATE TABLE IF NOT EXISTS firewall_membership( bash-5.1# grep 'CREATE PROCEDURE' linux_install_firewall.sql CREATE PROCEDURE sp_set_firewall_mode (IN arg_userhost VARCHAR(288), IN arg_mode varchar(12)) CREATE PROCEDURE sp_reload_firewall_rules(IN arg_userhost VARCHAR(288)) CREATE PROCEDURE sp_set_firewall_group_mode (IN arg_group_name VARCHAR(288), IN arg_mode varchar(12)) CREATE PROCEDURE sp_set_firewall_group_mode_and_user (IN arg_group_name VARCHAR(288), IN arg_mode varchar(12), IN arg_userhost VARCHAR(288)) CREATE PROCEDURE sp_reload_firewall_group_rules(IN arg_group_name VARCHAR(288)) CREATE PROCEDURE sp_firewall_group_enlist(IN arg_group_name VARCHAR(288), IN arg_userhost VARCHAR(288)) CREATE PROCEDURE sp_firewall_group_delist(IN arg_group_name VARCHAR(288), IN arg_userhost VARCHAR(288))
启用或禁用防火墙
可通过设置 mysql_firewall_mode 系统变量来启用或禁用防火墙。例如,在选项文件中添加
1 2 [mysqld] mysql_firewall_mode=ON
然后重启服务器使设置生效。
也可在运行时使用 SET PERSIST mysql_firewall_mode = ON; 或 SET PERSIST mysql_firewall_mode = OFF; 来设置并持久化防火墙状态。
1 2 3 4 5 6 7 8 9 10 11 12 13 mysql> SET PERSIST mysql_firewall_mode = ON; Query OK, 0 rows affected (0.00 sec) mysql> show variables like '%firewall%'; +----------------------------------------+-------+ | Variable_name | Value | +----------------------------------------+-------+ | mysql_firewall_database | mysql | | mysql_firewall_mode | ON | | mysql_firewall_reload_interval_seconds | 0 | | mysql_firewall_trace | OFF | +----------------------------------------+-------+ 4 rows in set (0.00 sec)
使用方法及具体例子
注册账户配置文件 :
先注册账户并将其置于 RECORDING 模式,
1 2 3 4 5 6 7 8 9 10 11 12 mysql> CALL mysql.sp_set_firewall_mode('mytest@localhost', 'RECORDING'); +-----------------------------------------------+ | read_firewall_whitelist(arg_userhost,FW.rule) | +-----------------------------------------------+ | Imported users: 0 Imported rules: 0 | +-----------------------------------------------+ 1 row in set (0.01 sec) Query OK, 0 rows affected, 1 warning (0.01 sec)
然后使用该账户连接到 MySQL 服务器并执行一些合法的 SQL 语句,以训练账户配置文件并建立允许列表。
例如,使用 mytest@localhost 账户执行 select * from information_schema.tables limit 1; 等语句,这些语句会被记录并用于构建允许列表。
切换到保护模式 :
当账户配置文件建立好后,将其切换到 PROTECTING 模式,
1 2 mysql> CALL mysql.sp_set_firewall_mode('mytest@localhost', 'PROTECTING'); Query OK, 0 rows affected, 1 warning (0.00 sec)
此时,只有符合允许列表的 SQL 语句才能被执行,其他语句将被阻止。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 mysql> select * from information_schema.tables limit 1; +---------------+--------------------+-----------------------------------+-------------+--------+---------+------------+------------+----------------+-------------+-----------------+--------------+-----------+----------------+---------------------+-------------+------------+-----------------+----------+----------------+---------------+ | TABLE_CATALOG | TABLE_SCHEMA | TABLE_NAME | TABLE_TYPE | ENGINE | VERSION | ROW_FORMAT | TABLE_ROWS | AVG_ROW_LENGTH | DATA_LENGTH | MAX_DATA_LENGTH | INDEX_LENGTH | DATA_FREE | AUTO_INCREMENT | CREATE_TIME | UPDATE_TIME | CHECK_TIME | TABLE_COLLATION | CHECKSUM | CREATE_OPTIONS | TABLE_COMMENT | +---------------+--------------------+-----------------------------------+-------------+--------+---------+------------+------------+----------------+-------------+-----------------+--------------+-----------+----------------+---------------------+-------------+------------+-----------------+----------+----------------+---------------+ | def | information_schema | ADMINISTRABLE_ROLE_AUTHORIZATIONS | SYSTEM VIEW | NULL | 10 | NULL | 0 | 0 | 0 | 0 | 0 | 0 | NULL | 2025-05-09 05:27:15 | NULL | NULL | NULL | NULL | | | +---------------+--------------------+-----------------------------------+-------------+--------+---------+------------+------------+----------------+-------------+-----------------+--------------+-----------+----------------+---------------------+-------------+------------+-----------------+----------+----------------+---------------+ 1 row in set (0.00 sec) mysql> select * from information_schema.tables limit 2; +---------------+--------------------+-----------------------------------+-------------+--------+---------+------------+------------+----------------+-------------+-----------------+--------------+-----------+----------------+---------------------+-------------+------------+-----------------+----------+----------------+---------------+ | TABLE_CATALOG | TABLE_SCHEMA | TABLE_NAME | TABLE_TYPE | ENGINE | VERSION | ROW_FORMAT | TABLE_ROWS | AVG_ROW_LENGTH | DATA_LENGTH | MAX_DATA_LENGTH | INDEX_LENGTH | DATA_FREE | AUTO_INCREMENT | CREATE_TIME | UPDATE_TIME | CHECK_TIME | TABLE_COLLATION | CHECKSUM | CREATE_OPTIONS | TABLE_COMMENT | +---------------+--------------------+-----------------------------------+-------------+--------+---------+------------+------------+----------------+-------------+-----------------+--------------+-----------+----------------+---------------------+-------------+------------+-----------------+----------+----------------+---------------+ | def | information_schema | ADMINISTRABLE_ROLE_AUTHORIZATIONS | SYSTEM VIEW | NULL | 10 | NULL | 0 | 0 | 0 | 0 | 0 | 0 | NULL | 2025-05-09 05:27:15 | NULL | NULL | NULL | NULL | | | | def | information_schema | APPLICABLE_ROLES | SYSTEM VIEW | NULL | 10 | NULL | 0 | 0 | 0 | 0 | 0 | 0 | NULL | 2025-05-09 05:27:15 | NULL | NULL | NULL | NULL | | | +---------------+--------------------+-----------------------------------+-------------+--------+---------+------------+------------+----------------+-------------+-----------------+--------------+-----------+----------------+---------------------+-------------+------------+-----------------+----------+----------------+---------------+ 2 rows in set (0.00 sec) mysql> select * from information_schema.tables where TABLE_SCHEMA = 'information_schema'; ERROR 1045 (28000): Statement was blocked by Firewall mysql>
监控与管理 :
通过查询 Performance Schema 防火墙表,可查看防火墙成员资格和白名单等信息。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 mysql> SELECT * FROM INFORMATION_SCHEMA.MYSQL_FIREWALL_USERS; +------------------+------------+ | USERHOST | MODE | +------------------+------------+ | mytest@localhost | PROTECTING | | fwuser@localhost | RECORDING | +------------------+------------+ 2 rows in set (0.00 sec) mysql> SELECT RULE FROM INFORMATION_SCHEMA.MYSQL_FIREWALL_WHITELIST WHERE USERHOST = 'mytest@localhost'; +-------------------------------------------------------+ | RULE | +-------------------------------------------------------+ | SELECT * FROM `information_schema` . `tables` | | SELECT * FROM `information_schema` . `tables` LIMIT ? | | SELECT @@`version_comment` LIMIT ? | +-------------------------------------------------------+ 3 rows in set (0.00 sec)
总结
MySQL Enterprise Firewall 作为一款企业级的数据库防火墙产品,通过其强大的功能和灵活的配置方式,能够有效保护 MySQL 数据库免受各种安全威胁,保障数据库的安全性和稳定性。本文对 MySQL Enterprise Firewall 进行了介绍和使用演示,希望对你有所帮助。
Have a nice day ~
– / END / –